In this digital age, our lives and businesses are connected and online. We’re all exposed to risks associated with cyberattacks, data breaches and even innocent mistakes. HR and recruitment teams may not appreciate the important role they play in effective cyber security, at least, not until something goes wrong. A data breach that exposes candidate or employee information is likely to result in financial and reputational loss. But, no matter your industry, whether you’re a multinational organization or a small-to-medium enterprise, your organization collects, stores, processes and transmits data. The majority of that data is sensitive and valuable!
The goal of cyber security is to manage the risks associated with the intentional or accidental destruction, modification or disclosure of your (or your organization’s) information and information systems. Cyber security can be applied in various ways, from administrative controls, physical security, user education and training, and technical controls.
Cyber security refers to the people, processes and technology that protect information from intentional or accidental destruction, modification or disclosure.
Perfect or total security is impossible; so the goal is to use these various cyber security techniques to reduce your organization’s risk to an acceptable level. Not only does the proper application of cyber security help to protect your organization’s information assets, it also helps your organization meet its compliance, insurance and legal requirements.
Download your free copy of the guide
In this guide
Navigate to:
- Recruitment, privacy and screening
- Onboarding, agreements and training
- Payment and payroll processing
- Offboarding
- Final thoughts
- About the authors
Introduction
The human element
Cyber security extends beyond systems and technology. At the end of the day, we’re only human and human error plays a part in cyber security risk. While malicious attackers are responsible for many of the security breaches that we read about in the news, a large proportion of security breaches are a result of human error.
| Case study: The January-to-June (2020) OAIC Notifiable Data Breach report shows that while the total number of notifiable breaches was down by 3% over the previous six months, breaches due to employee error were up by 37%! Security-awareness training will assist greatly in reducing the incidence of employee error. |
While many aspects of cyber security are technical in nature (and are not discussed here) HR and recruitment’s relationship with cyber security is much more to do with the teams’ powers and responsibilities: what do you know about the new people you are hiring? What information are you responsible for? And what can you do to protect yourself, your team and your organization?
In this guide, we’ll demonstrate why HR and cyber security do, in fact, go together, and why you should care about this increasingly important topic.
Cyber security and HR: Why does it matter, and what’s at risk?
A data breach happens when personal, sensitive or protected information is accessed, disclosed without authorization, or is lost. Data breaches (and their clean-up) can result in financial loss, increased insurance costs, litigation and fines, and significant damage to your organization’s reputation.
From the HR and recruitment teams’ perspective, loss of reputation can be devastating. The information that is collected by those teams includes personal and sensitive information related to both the candidates and the organizations that are looking to recruit new staff. A data breach that results in the disclosure or loss of this information will certainly impact upon the ongoing ability of the organization to recruit, engage and motivate candidates and clients alike.
Instead of viewing cyber security as a constraint, consider it instead as a market-leading edge that will help to build respect and empower your team. As an HR or recruitment professional, here are the main steps in the employee lifecycle you need to be mindful of when considering cyber security.
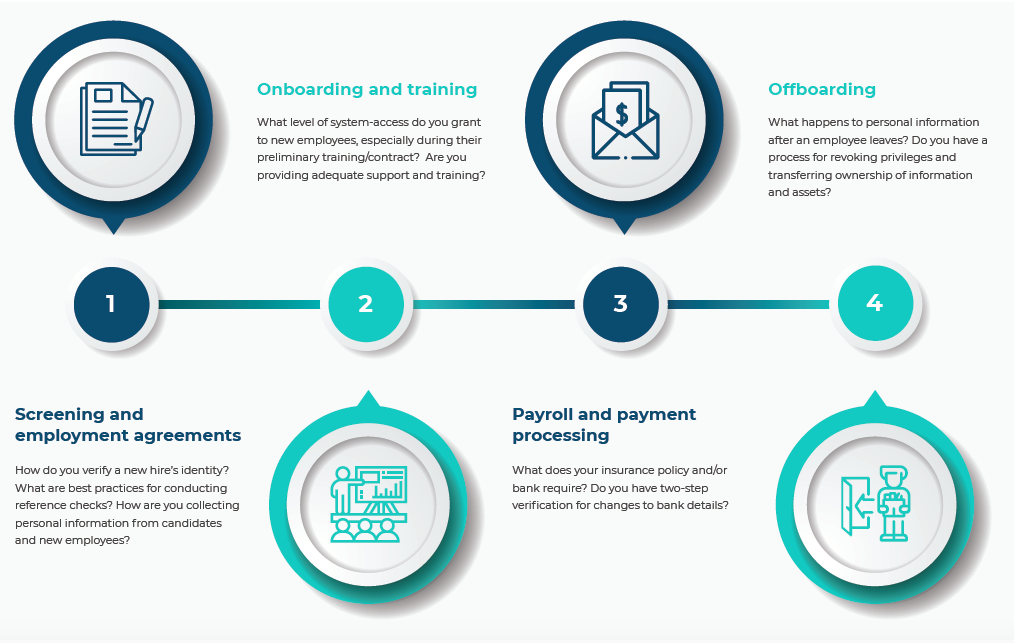
Let’s consider each of those four steps in turn.
Recruitment, privacy and screening
It all starts when you begin the recruitment process and start to collect information about candidates. Because you’re handling personal and sensitive information, keep in mind your moral and legislative obligations.
Take care when collecting, storing and processing personal information from candidates.
Australian Government agencies, organizations with an annual turnover of more than $3 million, and some small businesses have responsibilities under the Privacy Act (subject to some exceptions and described in the Act). For more details, visit the OAIC web site. For now, we’ll just cover a few key points.
An organization (as defined under the Privacy Act) that collects personal information about a candidate (for example, as part of their job application) has a number of responsibilities including:
- managing personal information in an open and transparent way – this includes having a clearly expressed and up-to-date privacy policy
- ensuring that the organization only (with some possible exceptions) uses or discloses personal information for a purpose for which it was collected.
- taking reasonable steps to protect personal information from misuse, interference and loss, and from unauthorized access, modification or disclosure.
A data breach happens when personal (possibly including sensitive) information is accessed, disclosed without authorization, or is lost. If your organization suffers a data breach and if the Privacy Act 1988 covers your organization or agency, you must notify affected individuals and the Office of the Australian Information Commissioner (OAIC) if the data breach involving personal information is likely to result in serious harm.
In order to avoid having to notify victims and the OAIC (while also appearing on tomorrow’s front page!) ensure that your organization has developed and applies robust and documented cyber security measures. If you’re unsure, talk to your organization’s information security officer or CEO, or engage a cyber security professional to ensure that your concerns are addressed sooner, rather than later.

Make sure you know who you’re talking to!
Your hiring process should include verification of applicant identities according to your organization’s documented policy and procedures. You can do this by:
- sighting identity documents (such as their driver’s license, Medicare card, passport, Visa/right-to-work documents and/or birth certificate)
- background and qualification checks
- national police checks
- employment verification/reference checks.
The exact methods that your organization uses should be documented in relevant policies and procedures; when developing those policies and procedures, your organization should consider referencing the Australian Standard – Employment Screening AS 4811-2006 which recommends that the level of screening assurance for a position be determined by a risk assessment for the position. For example, police checks may be required for a position of authority with substantial financial responsibilities, but not for an entry-level position
Remember, however, that as per the preceding point, all this personal information needs to be properly and securely collected, used and protected!
| Case study: Over the years a number of people in Australia have been charged after being found to have been employed by Australian hospitals even though they possess no medical qualifications. People like Shyam Acharya worked at and were paid by Australian hospitals, sometimes for years on end, almost certainly as a result of failings in the new-staff identity-verification processes. Acharya is now on the run having been convicted and fined $30,000 if in absentia; he’s believed to have fled overseas after faking his citizenship, forging a passport and medical qualifications that he stole… from a real doctor! |
Find out more about Scout Talent’s Candidate Management System, :Recruit.
Background checks are an important, but sometimes overlooked, part of the recruitment process and national police checks allow you to be confident that you are aware of any relevant, previous criminal issues. Thorough background and police checks may also be required for certain contracts and insurance policies.

A note on reference checks
Candidate reference checks are an opportunity to separate fact from possible fiction. When performing a reference check, don’t rely on the referee’s contact details that are provided by the candidate. Instead, consider contacting the referee by some “out of bands” means, such as by calling an organization’s central number. This allows you to verify the referee’s identity and once again be sure that you know who you’re talking to.
Also, remember to obtain at least three references. (Note: Some candidates may not list a reference from their most recent employer, if they haven’t spoken to them about wanting to move on. You’ll need to take this into account and consider other options.) The so-called “wisdom of crowds” is real. It’s worth getting as complete an understanding of the candidate as possible.
Onboarding, agreements and training
So, you’ve verified your ideal candidate’s identity and they’ve accepted your offer. Congratulations! While this is an exciting part of the process, there are some things you need to keep in mind when onboarding new staff.
Incorporate your policies and procedures
You should include or explicitly refer to (and make available) your organization’s information security policy, acceptable use policy and privacy policy in all your employment agreements for two reasons. Firstly, because doing so ensures that the new employee understands his/her obligations and also understands that your organization takes cyber security seriously. And secondly, doing so provides you and your organization with protection. If an organization cannot show that the employee understood and agreed to the organization’s cyber security policies and procedures, the organization will be limited in the disciplinary actions that can be undertaken in the event that the employee is responsible for a policy breach; this, in turn, may expose the organization to financial and legal consequences.
| Monitoring and agreements. Any organization that has a mature cyber security program in place will monitor system and network activity, and will retain logging data for future analysis. The goal of this monitoring is to allow the organization to detect and respond to malicious activities in an effective and timely manner. While there is nothing sinister in using log-collection and analysis to protect the organization, the HR and recruitment teams will need to ensure that employment agreements note clearly the extent to which a user’s activities are being monitored, and what the activity logs are being used for. In addition, the employment agreement that is signed by the IT team members should note clearly the responsibilities and expectations surrounding the use and security of this sensitive data. You should consult your legal team and ensure that the employment agreements cover this important point. |
Clearly inform your IT team about what is needed
Your IT team will need to provision an account for the new employee, and grant that person privileges and permissions so that they can access the information and systems that they need for their job. The HR and recruitment team needs to provide that information to the IT team clearly and succinctly, so consider the best way to define the new employee’s roles and responsibilities.
Maintain an updated and interactive security awareness training program
It is a well-accepted fact that general security-awareness training is the cornerstone of any effective information security practice; if people don’t know how to do their job securely, all the technology in the world won’t keep attackers at bay. One area where employee awareness is critical is in preventing phishing attacks.
| A phishing attack takes place when an attacker tricks their victim into sharing sensitive information such as usernames, passwords and credit card details. The attacker generally tricks the victim by pretending to be a trustworthy entity, most commonly in an email or SMS message. |
According to the OAIC, data breaches resulting from phishing continue to be the leading source of malicious attacks. While it’s been common-place for attackers to build on phishing attacks by using ransomware to encrypt or destroy the victim’s information, attackers now extend their attacks by publicizing stolen information across the internet if their ransom is not paid.
HR and recruitment teams should be responsible for providing all employees with periodic (at least annually), adequate training. But remember, success depends on the full participation and support of senior management, because training needs to start at the top!
Great training can be delivered through online learning platforms and webinars. When you’re in the market for a new cyber security course, don’t just settle for an off-the-shelf training module! Your security-awareness course should be customized based on your organization’s requirements, and should refer to organization-specific structures, policies, procedures and business practices. Without this customization, awareness training courses will be too generic and ineffective.
| Tip: Check your insurance policy! Many policies require an organization to ensure that all employees undertake regular cyber security awareness training. If your organization does not have an adequate training program in place, the insurer may levy a hefty excess and/or increase premiums in the event of a claim. |
Consider testing as well!
The HR and recruitment teams should consider using a Learning Management System (LMS) so that it’s possible to track your employees’ progress and gain better oversight. In offering training, you may require all staff to receive a “passing mark”, and you should use the LMS to record the frequency and success (or failure!) of all employees’ training attempts. If your organization doesn’t already have a suitable LMS, don’t panic! There are plenty of useful LMS services available at reasonable prices.
Consider testing your employees by arranging social-engineering assessments where skilled cyber security experts will conduct tests that will see how well employees respond to simulated phishing (and perhaps other social-engineering) exercises such as:
- email-based attacks.
- attacks that attempt to reveal sensitive information over the phone.
- attempts to change payment or banking details, or process counterfeit invoices.
Testing is the best way to reinforce training and it will allow the HR and recruitment teams to determine the level of success of the training program.
Find out more about onboarding software.
Payment and payroll processing
As we discussed at the introduction to this guide, a wide range of personal and sensitive information will be collected from candidates, and even more information will need to be collected once the successful candidate begins their employment. This information may include, for example:
- bank and super account details
- medical information
- next of kin contact information
- date of birth and address.
As outlined above, you should (even if your organization is not bound by the Privacy Act) collect, store and process this personal and sensitive information in line with the Australian Privacy Principles (APPs). And ensure that there are procedures in place to destroy that information securely when there is no longer a legitimate reason to retain it.

A note on payment and payroll processing
Your organization should have in place a policy and associated procedures that govern the changing of any payment or banking details. All too commonly, attackers are able to masquerade as a person or a business (remember the phishing discussions above!) and convince an organization to change payment, invoicing, banking or other financial details. If the attacker is successful, the victim organization will transfer funds to a bogus account; in this situation, not only is the victim organization poorer for the experience, they also suffer reputational loss as the legitimate payee becomes aware that their details have been fraudulently altered.
Establish a two-step process for changing financial details so that it’s not possible for an attacker to succeed by targeting just one person and apply this process to your employees, just as you would when changing bank account details for the organization’s suppliers.
Offboarding
Nothing lasts forever and at some point, employees will leave your organization either voluntarily or as a result of some management or supervisory decision. Whichever the case, HR and recruitment teams have some final cyber security responsibilities that need to be addressed at the cessation of employment: responsibilities, which are in fact, critical to the ongoing security of the organization.
A final reminder is in order
Ensure that the offboarding process includes a step where the soon-to-be-ex-employee is reminded of, and acknowledges in writing, the obligations and responsibilities that they agreed to in their original employment contract. Ensure that the employee’s termination-of-employment letter includes a clear description of the person’s ongoing obligations. First of all, that they agreed to the organization’s information security policy, acceptable use policy and privacy policy. And secondly, that they agreed to the conditions under which they were given access to the organization’s information and systems. Your legal department will be able to provide you with precise wording, as was the case for the employee’s original employment contract.
Of course, you want to maintain an amicable, positive relationship with your departing employee. Use this tactful strategy to achieve that goal, while also protecting your organization by being legally prepared should a worse-case scenario arise; then, the ex-employee would become responsible for a data breach after their departure.
Initiate revocation of rights and privileges
What processes and procedures do you have in place for when employees leave your organization? Establish a set of processes to de-provision their system access.
Ensure your IT team knows how they should delegate access to the ex-employee’s information and services. This should be part of the documented off-boarding process, so that information is not lost because an account or profile is deleted without reassigning ownership of the account assets.
Prepare for deletion and delegation
Your organization originally collected the employee’s personal (and perhaps sensitive) information for a specific, documented and agreed purpose. Ensure that there are processes in place so that your organization only retains that personal information in line with what was originally agreed.
| Case study: An Australian hospital stored medical history and next of kin contact information for ex-employees that had not worked in the organization for more than 10 years. The hospital faced a data security incident, where this information was breached. This negatively impacted their ex-employees, as well as their next of kin contacts. The hospital faced devastating legal and financial consequences, as this PII was not kept within legitimate, acceptable or declared use. |
Download your free copy of the guide
Final thoughts
While many aspects of cyber security are technical in nature, HR and recruitment team’s relationship with cyber security is much more to do with the team’s powers and responsibilities. This is especially true when it comes to the management of personal and sensitive information, and to the education and management of employees from the time they apply for a position, to the time they end their employment.
A data breach happens when personal, sensitive or protected information is accessed, disclosed without authorization, or is lost. Throughout this guide we’ve presented a number of cyber security measures that HR and recruitment teams can put in place to reduce the risks associated with a data breach (and the resulting in financial loss, increased insurance costs, litigation and fines, and significant damage to your organization’s reputation). These measures can be applied at various stages of an employee’s employment life cycle. This includes during:
- recruitment – when you’re collecting personal and sensitive information, and when you need to be certain about who you’re engaging with
- onboarding – (and as the new employee settles in), particularly when ensuring that policies and procedures are understood and agreed to, and as you deploy (and test!) security-awareness training programs
- payment processing – while you manage the employee’s financial, personal and payment information
- offboarding – when (and after) the employee leaves the organization.
From an HR perspective, a data breach that results in the disclosure or loss of personal and sensitive information will certainly impact upon the ongoing ability of the organization to recruit, engage and motivate candidates and clients alike. With that in mind, we hope you’ve gained value from this guide. More importantly, we hope that instead of viewing cyber security as a constraint, you now consider it to be a market-leading edge that will help to build respect and empower your HR/People team.
About DotSec
DotSec is a professional information security organization. Since the late 20th century, we have assisted clients across most industry sectors and across all tiers of government to do more business, more securely.
DotSec is a Payments Card Industry (PCI) Qualified Security Assessor (QSA) company and provides ISO/IEC 27001 implementation and preparedness services. DotSec provides audit and remediation advice for APRA’s CPS 234 and ACCC’s CDR. We have a strong IRAP history, assisting companies to become compliant with controls from Australian federal government’s Information Security Manual (ISM) and Protective Security Policy Framework (PSPF).
DotSec infosec professionals are certified AWS and Splunk Architects and have a strong history in the design, delivery and management of secure-hosting services for national brands and government.
About the authors
 Dr. Tim Redhead
Dr. Tim Redhead
Tim established DotSec in 1999 and since then, he’s enjoyed working with outstanding cyber security experts, delivering top-quality information security products and services. Tim has over 20 years of infosec/cyber security experience and continues to coordinate innovative projects that support and secure clients in most industry sectors, as well as across all tiers of government. Tim speaks at conferences, seminars and trade shows; feel free to get in touch with him and learn how DotSec can help you do more business, more securely.
 Victoria McGlynn
Victoria McGlynn
Victoria McGlynn is an Employer Branding Specialist and Marketing Content Producer for Scout Talent Group. Throughout her professional experience, she has used effective storytelling and an authentic voice to help organizations achieve the best business outcomes through crafting effective copy.
In addition to producing marketing and advertising copy, her writing has been awarded, shortlisted, and featured in various recruitment, fashion, culture, lifestyle, and professional publications. She is passionate about reading, writing, sharing and learning.